In this article, which is the first part in our tutorial series on
how to set up a home hacking and security testing lab, we will walk through the creation and installation of a Kali Linux virtual machine inside VirtualBox. This system will then function as our main monitor and attack machine in subsequent tutorials. After setting up the virtual system, we will:
- run a live Kali session
- do a full install
- update the system
- install the VirtualBox Guest Additions
- configure appropriate user accounts
- and finally switch over to a bridged network adapter in preparation for the next tutorial in the series
The whole process may take a few hours to complete, more or less, depending on the specifics of your own situation, ex. computer, internet connection speed, and so on. This session took me about three hours from beginning to end.
Virtualization
There are a number of different free
virtualization packages available online. For this tutorial series, we've chosen to go with
VirtualBox because it's open source, beginner friendly, and there is a lot of documentation and support information that can be found for it online, especially regarding the systems that we will be installing. For example, since Kali and Metasploitable are derived from the Debian Linux distribution, support information on other Debian-based operating systems such as Ubuntu or Crunchbang is often also applicable to Kali and Metasploitable, as we shall see in this and subsequent articles.
The first step is to download and install the
VirtualBox software package onto the primary computer chosen for your lab setup. Make sure you
download the right version for your operating system and hardware architecture (32 bit vs. 64 bit).
Instructions for installation on various operating systems are readily available if you run into any snags. Also make sure to keep a handy copy of the
VirtualBox user manual, which comes packaged with the software and can also be found online.
Once you install VirtualBox and run it for the first time, you'll be presented with the application's welcome prompt, which provides an orientation for the interface. Poke around in the menus to get a feel for the software.
Next,
download a copy of the Kali Linux operating system .iso disc image. Again, make sure you download the proper ISO file for your computer's architecture. Depending on the speed of your internet connection, this may take some time, as both the 32 bit and 64 bit files are 3GB in size. Kali's documentation can be found
here.
As Kali is a security sensitive system, once you have downloaded the file, it is recommended to check its SHA1SUM hash value against the one supplied on the download page to make sure the file had not been corrupted in transit. For more on
how to check a file's hash value, follow the link to our previous article providing an overview of the process.
If you plan on playing around with a number of different virtual guests on your computer, it is probably a good idea to create a permanent folder somewhere on your system where you will keep all the necessary operating system .iso files.
Creating a Virtual MachineNow let's return to VirtualBox and set up the virtual machine on which we will install the Kali operating system. Open VirtualBox and click "New". Provide a name for your Kali virtual guest system. Choose Linux as the type and Debian as the version, since Kali is derived from Debian Wheezy. As you can see below, I'm using the 32 bit version. Click Next.
Choose the amount of memory you want to allocate to the virtual instance once it is up and running. In my experience, Kali can use a lot of RAM, and the computer I'm running it on has a fair amount to spare, but for now I'm going to leave it at the default of 512MB. You can also adjust these settings later to optimize them for your own setup. In my experience, Kali runs pretty well in VirtualBox even on a laptop with only 4GB of RAM, though you may have to conserve by shutting down memory intensive applications running on the host computer. After you've set your memory size, click Next.
Choose whether you want to create a virtual hard drive for the virtual machine. We're going to need one for our home lab, so check "Create a virtual hard drive now", then click Create.
For the "Hard drive file type", check "VDI (VirtualBox Disk Image)", then click Next.
In the "Storage on physical hard drive" window, you'll probably want to choose "Dynamically allocated." This means that space will not be taken up on your physical hard drive until it is actually written to the virtual disk. If you choose "Fixed size" then the virtual disk drive will take up a set amount of space on your physical hard drive even if that space has not been written to by the virtual machine. Click Next.
In "File Location and Size," choose where you want the hard drive files for the virtual system to be stored by clicking on the folder icon. I just use the default folder. This is where VirtualBox will store all files related to your virtual machine. Also, on this screen you may increase or decrease the amount of hard drive space you want to be allocated for the virtual instance. 8 GB is the default. I'm going to push mine up to 10 GB. Click Create.
The new virtual system should now appear in your Virtualbox interface. As you can see I have three folders in my left sidebar, and have placed the kali1 instance I just created into a new "lab" group. In the main interface we can see the settings for the new systems, which are a mixture of defaults and configuration settings we determined ourselves in the creation phase. Before starting up the instance for the first time, I usually adjust a few settings first.
Click "Settings" for your new virtual machine. I'm going to add a description under the General menu, because I have other Kali instances on my computer.
In the System menu, under Motherboard, I uncheck "Floppy" in the boot order.
Also in the System menu, under the Processor sub-menu, we
have to check "Enable PAE/NX" for Kali to operate properly.
Finally, under the Display menu, I add more Video Memory to the default 12MB, bumping it up here to 36 MB to start. Again, this can be adjusted later to optimize your particular setup.
That's it for now. Browse through the other menus. Notice in the Network setting we can add up to 4 different network adapters for our virtual machine. Later we will play around with the network setting, after we've fully installed the Kali operating system. For now, a single network adapter running on NAT (i.e. Natural Address Translation) will suffice for our purposes.
Click "OK" to save your changes.
Fire up your new machine by double clicking it, or single clicking it and then clicking Start. You will be prompted to "Select start-up disk". We now have to choose the startup disk for our new virtual machine. This is the Kali .iso file we downloaded earlier. Click the folder icon and navigate to the folder where you've stored the Kali .iso file on your host computer. Select it, then click start.
Booting into a Kali Live Session Kali should boot as if you were booting a real physical machine from a cd with the Kali operating system file on it. Notice that if you click inside the guest window, your mouse pointer will be "captured" by the guest. From then on, your keyboard and mouse activity will control the virtual machine. To switch back to using your host machine, you have to hit the host key, which by default is Right-Control on my computer. It may be different depending on your operating system. The Virtualbox interface will tell you what the "Host Key" is in the bottom right of the window.
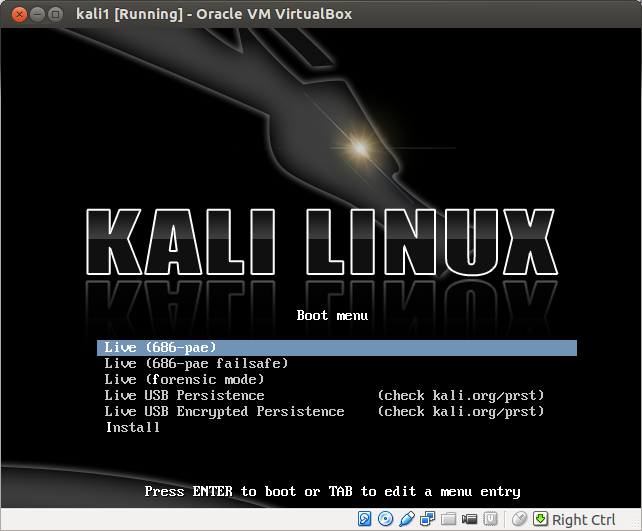
From this menu, you can boot into a number of different types of live session, or you can do a full install of Kali on the virtual hard drive we previously created inside Virtualbox. As we shall see, there are numerous advantages to doing a full install of Kali for the purposes of our home hacking lab, but one of the advantages of a live session is that we can jump right in without any further configuration. Let's select the default Live session. Here is the Kali Desktop after booting into live session (note the time and day, yes, this is how I prefer to spend Saturday evening):
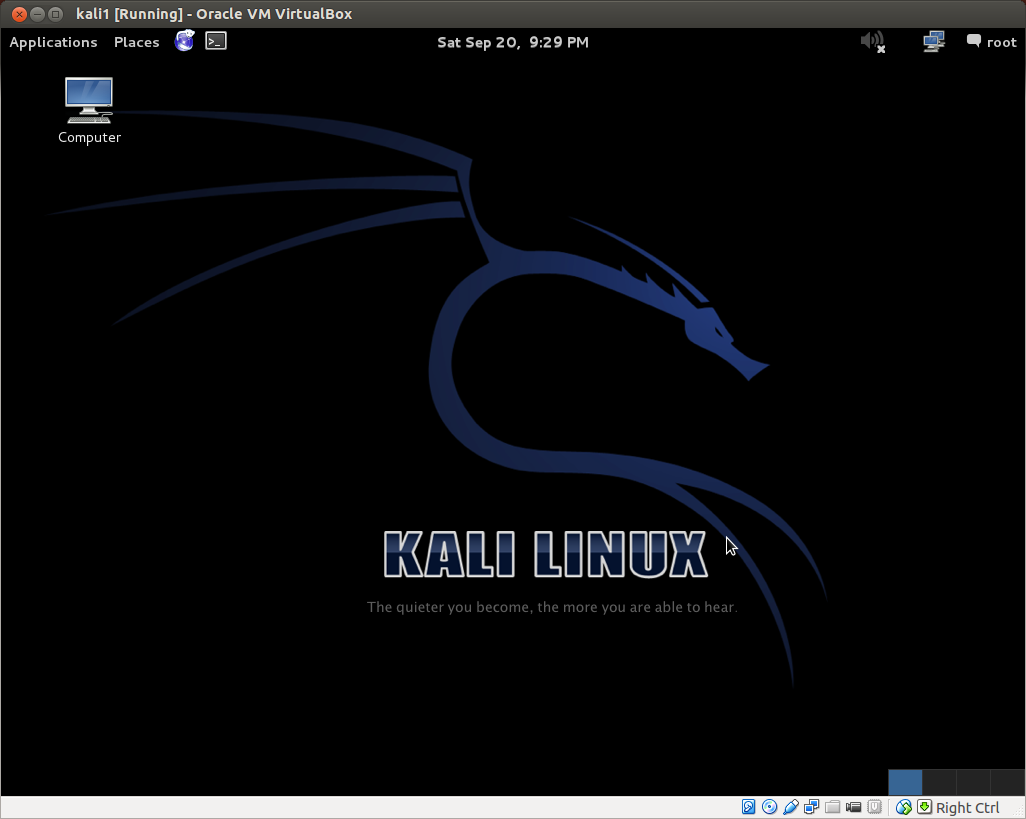
You will soon notice that there are certain limitations to the virtual machine's interface. For example, your mouse wheel will not work, you cannot enlarge the size of the screen, or go full screen, there is no tab completion in the terminal, and there are other interace issues as well. This is not a limitation of the live session, or Kali itself, but rather of the virtual machine we've created. However, all these issues can be addressed by installing the Virtualbox Guest Additions, but we'll save that for our future full install of the system.
Notice also that there are limitations to the default NAT networking interface. Under NAT (natural address translation) the Kali guest is not treated as its own independent node on the wider local area network. It does not have an independent ip address on the local area network. Its virtual ip address is translated by the ip address of the host machine. This can be addressed by adding a second network adapter to the virtual system or changing the present one, as we shall see later on.
However, despite these limitations, you can already begin exploring the ridiculous number of tools that come bundled with Kali. Here are Kali's Top Ten Tools:
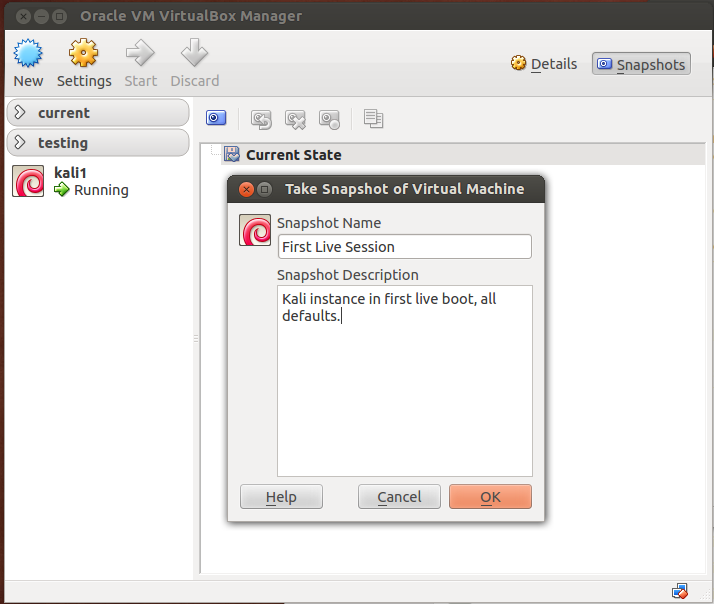
Since all appears to be working well, let's take a snapshot of the virtual machine. VirtualBox snapshots are a way to keep a log of your virtual machines in a given state. If you are experimenting with a new configuration, and everything suddenly goes to hell, you can always revert back to your previous snapshot like nothing happened. Go to the VirtualBox interface window, select your Kali guest, click "Snapshots" in the upper right. Take a snapshot by clicking on the camera icon. Name the snapshot, and give it a description. Now, if we seriously screw up something on the machine, we can always just revert to this prior state of the system.
Now let's reboot to do a full install. Click the root menu item in the top right of the Kali Desktop window. Then choose reboot or do a full shut down and boot from the VirtualBox interface. In the process, you will be prompted to remove the disk from the system. Of course, we are using a virtual disk image, so there is no physical disk that needs to be removed. Just click enter to continue. Now reboot . . . OH NO!!!!! "FATAL ERROR: No bootable medium found! System failed."
If you've been following along thus far, you've likely just been delivered this disturbing warning by your virtual machine upon reboot. It's a good thing we took that snapshot! Actually, this was only to be expected. Remember when you had to remove the virtual disk from the machine upon shutdown or reboot? Well, we now have to re-insert the virtual disk, that way we can reboot into Kali and move on to a full install of the operating system. So solve this "Fatal Error," with your virtual machine still running:
- Point your mouse toward the Oracle VM VirtualBox application menu on your host machine and find the Devices dropdown menu
- Select "CD/DVD devices"
- Select "Choose a Virtual CD/DVD disk file..."
- Select or navigate to your Kali .iso operating system file
- Close the virtual guest by exiting the window and powering off the machine
After the machine closes down, restart it from inside VirtualBox, it should boot into Kali from the newly inserted virtual disk.
Full Installation of Kali in VirtualBox Now let's move on to our full installation of the Kali virtual instance. Once your system reboots into the main menu, choose the Install option and hit enter.
The installation process will begin straight away. Note that over the course of the installation, the various menus are not graphical interfaces. You cannot point and click, you have to enter info via the keyboard, and use the arrow keys to navigate. We're not going to do anything fancy here for the purposes of this simple home lab setup. In most cases the defaults will suffice. Simply follow the directions on each page. This process took about an hour on my computer. Here's the first screen:
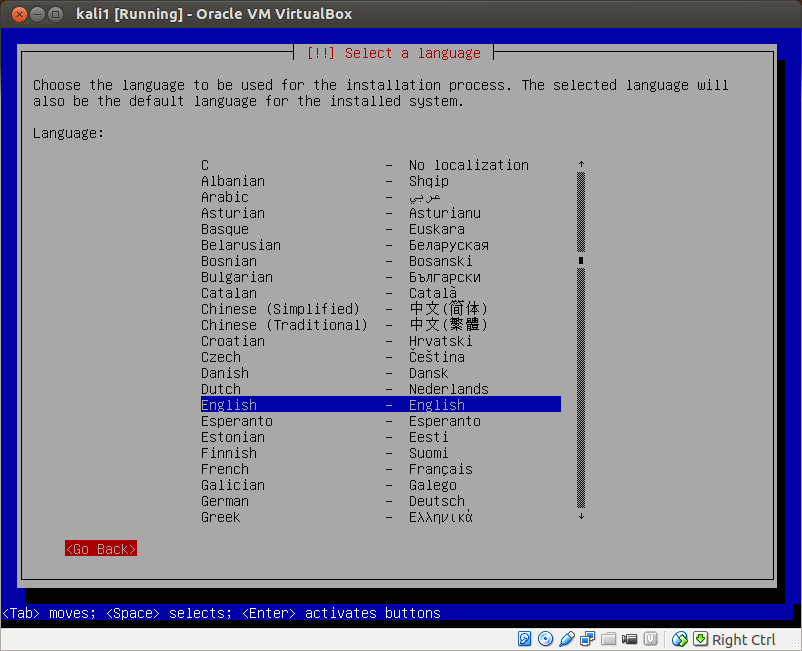
- Choose your language.
- Select your location.
- Select your keymap.
- Enter the new host's name. It simplifies things to choose the same name you chose for your VM inside VirtualBox, but these need not be the same name. You can also always change both names later if you so wish.
- Enter a domain name. I'm going to leave it blank and hit enter.
- Enter a root password, then re-enter to confirm. These will be the credentials for the root super-user on the system. Be sure to make a note of the password you've chosen.
- Select your time zone.
- Partition Disks, select 'Guided - Use Entire Disk'. Not to worry, here 'Entire Disk' means the virtual hard drive we created upon initial setup of the VirtualBox machine. In my case, this will eventually claim up to 10GB on my harddrive, as this was the size I specified when I created the VM.
- Select disk. This is the virtual hard drive we configured earlier.
- Select partition scheme. Let's choose default, all files in one partition.
- Confirm selections, or go back if necessary.
- Select yes, to commit the changes by writing them to disk.
- Select network mirror if any. None is needed for this home lab setup.
- Select proxy if any. None is needed for this home lab setup.
- Install grub boot loader (default).
- Installation complete! Select continue.
Let the machine do its thing, and then reboot the system. Upon reboot, log into kali using 'root' as your username along with the password you chose for root during installation.
Congratulations, you now have a virtual instance of Kali Linux installed on your computer! But we're not done with our configuration of the new virtual machine just yet. We still have to update the software on the system, and then we're going to install the VirtualBox Guest Additions in order to enable full screen mode, tab completion in the terminal and so on. This process might take you another hour or so, depending on your internet connection.
Updating Kali and Prepping for Guest AdditionsIf your host computer is connected to the internet, you should have internet connectivity from inside your Kali VM over your NAT adapter. You can check this by opening up the bundled Ice Weasel browser and making sure you can get online. Ice Weasel can be opened by clicking the icon next to the Places drop down menu in Kali. You can also try pinging google.com or some other website from inside a terminal. You can open a terminal by clicking the terminal icon next to the Ice Weasel icon. We are going to need a working internet connection to update the system.
Let's update the system. Open a terminal in Kali and enter the following command:
apt-get update
This will make sure Kali checks the most recent repository for any software updates. Once this process completes, enter:
apt-get dist-upgrade
This will update all software on the Kali system. Depending on your internet connection, this may take some time. The process lasted around 15 minutes for me this time around. Once that is complete, you now have a fully updated Kali virtual machine. But we are still lacking some basic functionality, so now we're going to install the VirtualBox Guest Additions.
Installing Guest Additions in VirtualBox can be tricky. To prepare the system to handle the Guest Additions, we have to run a couple more commands inside the terminal, so open up a new terminal shell and run the following series of commands, one after the other, after each completes:
apt-get clean
apt-get autoclean
apt-get update
apt-get install build-essential linux-headers-`uname -r` dkms
Notice that `uname -r` is inside backticks, not single quotes in the final command here. Yes, this matters. The backtick key should be located just above the tab key on your keyboard. This series of commands was suggested on
this CrunchBang forum post, and it has yet to fail me in setting up Guest Additions for a Debian-based machine inside VirtualBox. Once this process has completed, we can now install the Guest Additions themselves.
Installing VirtualBox Guest Additions in KaliWhile engaged in the Virtual system, in the Oracle VM application menu, go to the Devices dropdown menu again. Notice the "Insert Guest Additions CD" option. Select it. You will get a pop-up inside Kali asking you if you want to run the file. If it succeeds, great! If not, that's not a problem. In my experience, it has never worked off the bat, so I click cancel.
Selecting the "Insert Guest Additions CD" menu option has inserted a virtual disk into your virtual machine. The files on this disk can be found in the folder: /media/cdrom/. Confirm that they are there by navigating to this folder in the graphical file system manager or in a terminal.
To install the Guest Additions for Kali, we need to run the VBoxLinuxAdditions.run file on the Guest Additions cd. However, you cannot simply run the file from the /media/cdrom/ directory. First we need to copy it and change its permissions.
Copy the file to your Desktop from inside a terminal with the following command:
cp /media/cdrom/VBoxLinuxAdditions.run /root/Desktop
You should see a copy of the file appear on the Desktop. Change to the Desktop directory inside the terminal:
cd /root/Desktop
Change the permissions on the file with the following command:
chmod 755 VBoxLinuxAdditions.run
Run the additions file:
./VBoxLinuxAdditions.run
Success? Success!
If you experience any snags along the way here, you'll have to do some trouble shooting. There is a ton of info online regarding installation of Guest Additions in VirtualBox VMs, likely in large part because the process can be tricky. Remember also, that support info for other Debian-based systems such as Ubuntu and CrunchBang will also apply to Kali in many cases. But the series of commands above has yet to fail me.
Upon successful installation of the Guest Additions, we have to shut down the machine for the updates to take effect. Reboot and log in as root again. Once the system reboots, the simplest way to confirm that the Guest Additions have been successfully installed is to see if you can maximize the window for the guest system. You should now also have code completion in the terminal, among other things. You can now eject the Guest Additions virtual CD from the Virtual cd drive. Click the Computer icon on the Desktop, then click eject under the devices menu.
We now have a fully updated fresh install of a Kali virtual machine with the VirtualBox Guest Additions installed. Let's shut down the machine, take a snapshot and switch the network adapter into bridged mode in preparation for the next tutorial.
Switching to Bridged NetworkingAfter the VM has shut down and you've taken your snapshot, open up the settings of your new virtual system and go to the Network menu. Unless you've already chaned these settings, you should have network Adapter 1 enabled, and attached to NAT. Change the attachment to a bridged adapter. This will allow our guest to act as an independent host on our local network, rather than have its address translated by the host computer the virtualization software is running on.
Finally, the adapter Name has to connect up to the appropriate network adapter of the
host machine, i.e. the one that is actually connected up to your local network, whether it is a wireless connection, an Ethernet connection, or whatever. The appropriate one should be selected by default. Click Okay.
Start up the guest. Open a terminal and ping a known website or host, or use a browser to visit a web page. If it works, CONGRATS! You're in bridged mode.
If you have no networking capability, and can't even ping other computers on your home network, let along a website. You have to do some trouble shooting. Here are some troubleshooting questions:
- Are your networking settings correct in VirtualBox?
- Is the adapter for the guest machine connected to the right interface on the host computer?
- Is Kali's /etc/network/interfaces file structured properly?
- Is the appropriate interface up as indicated by ifconfig?
- Have you tried restarting Kali's networking service?
- Is Kali's /etc/NetworkManager/NetworkManager.conf file structured properly?
- Have you tried restarting the network-manager service?
As the old saying goes, when all else fails, read the manuals! Setting up an Administrator Account If you've followed along this far, you are now logged into your Kali VM as root, have a fully updated system, and the VirtualBox Guest Additions installed. It is not good to get into the habit of running everything in Kali as root. Best practices dictate setting up an administrator account and using sudo to run security-sensitive commands.
Create an administrator account by going to the root dropdown menu in the top right of the Kali Desktop. Then select: root => system settings -> user accounts -> create an administrator account. Create an administrator account with a separate password. Then log out, and log back in with your new admin account. Using an administrator account such as this creates a bit of extra work (ex. having to use sudo for otherwise everyday commands such as ifconfig, having do to a bit of extra configuration for applications such as Wireshark and Zenmap), but it is a good habit to get into so as to avoid becoming careless with the root account. After setting up an administrator account, shut down the machine and take another snapshot.
In
part two, we will use two tools bundled in
Kali to explore your home local area network. Thanks for following along. As always, leave any questions or comments below.
Source:http://blog.agupieware.com/2014/10/hack-lab-part-1-installing-kali-linux.html































